Governance, Risk & Compliance Simplified
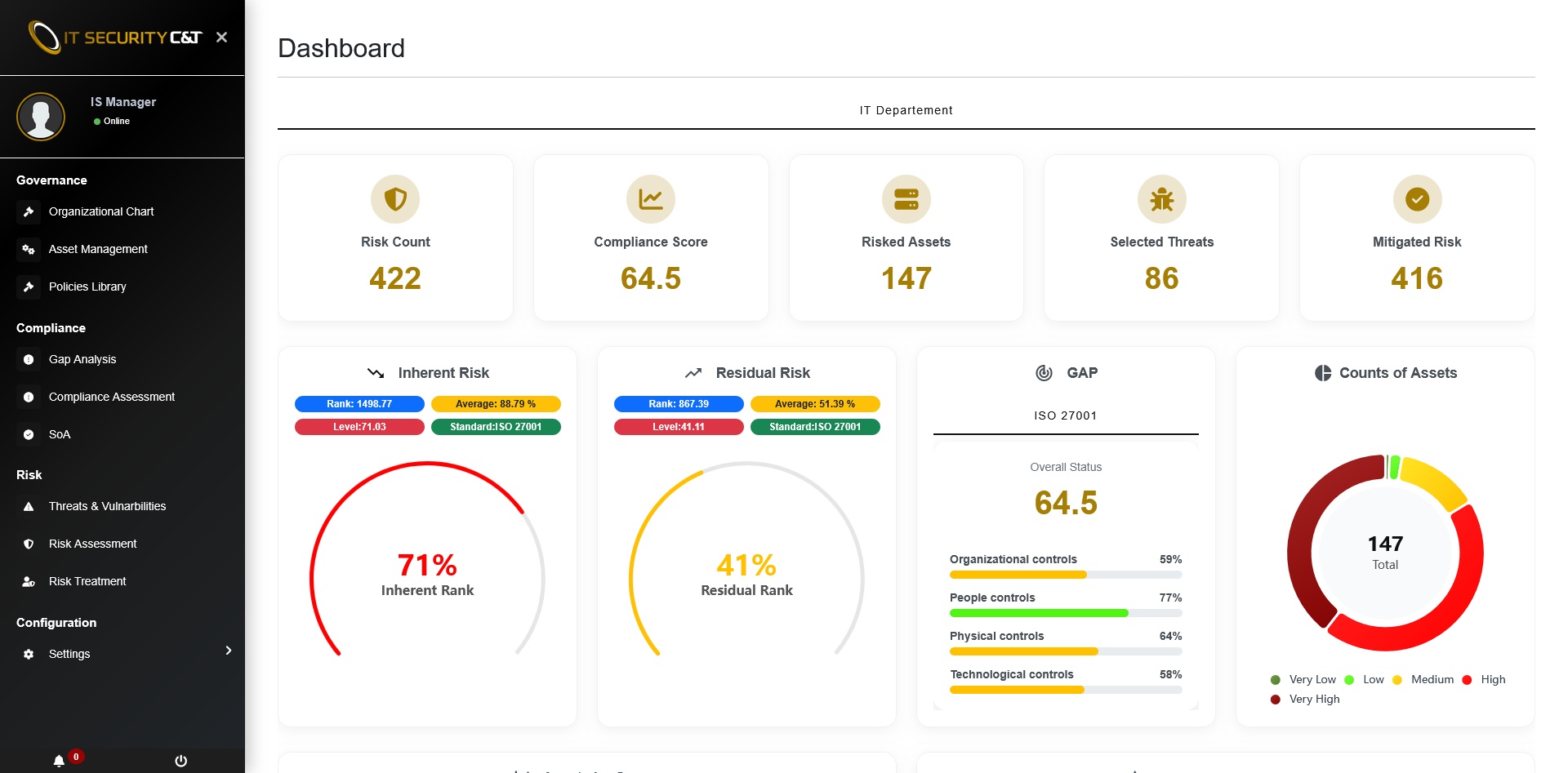
GRC stands for Governance, Risk, and Compliance—a unified approach to managing organizational integrity. Our tool streamlines policies, assesses risks in real-time, and ensures seamless regulatory adherence.
- Unified approach to governance, risk, and compliance
- Real-time risk assessment and monitoring
- Seamless regulatory compliance management